TrueBot Malware: The Infection of Businesses
-
Mohammad Alhummada
- 14 Dec, 2022
- 01 Min read

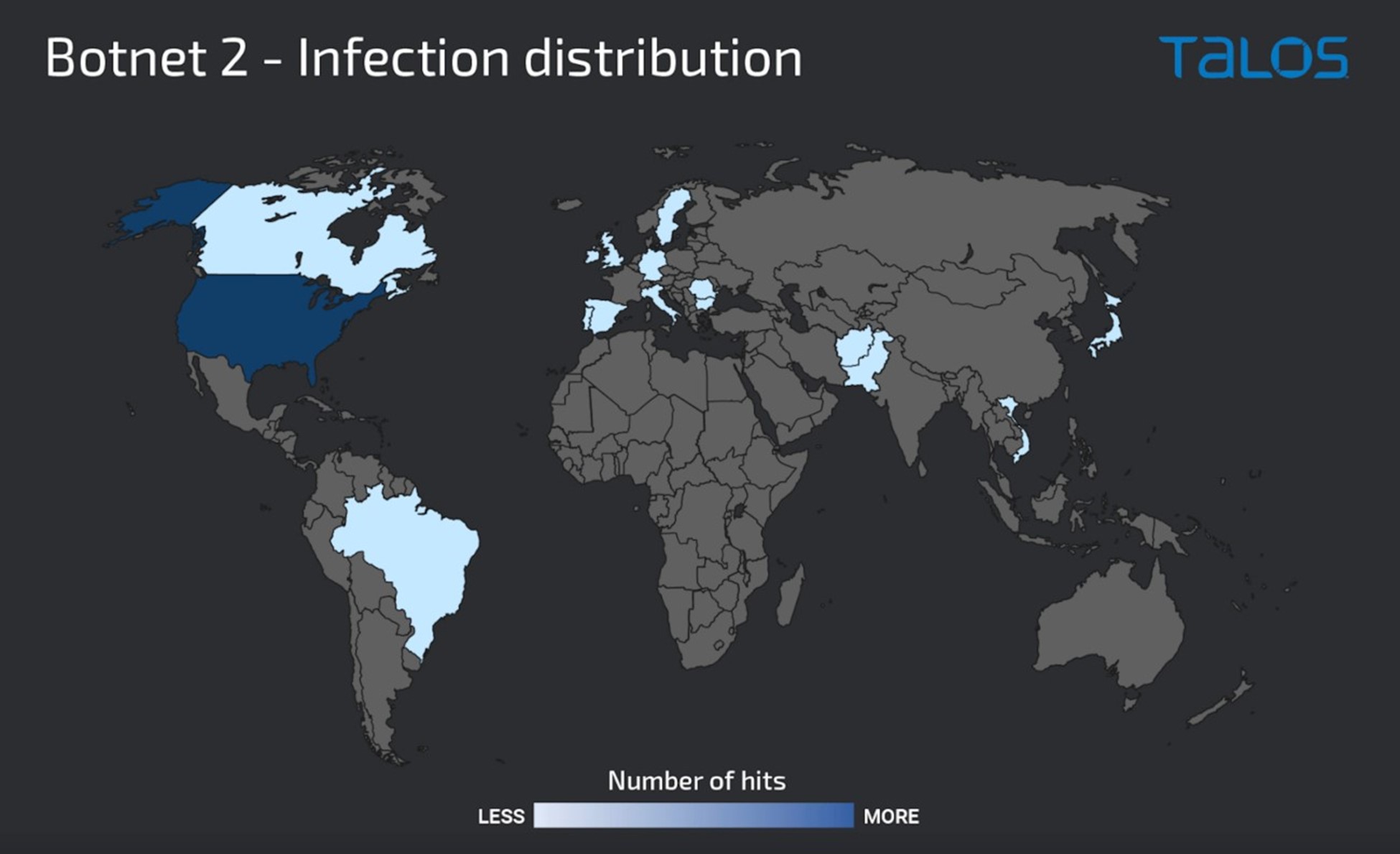
Cisco Talos reveals found infamous TrueBot malware and hits the U.S with additional attached infamous Clop ransomware.
What is this?
TrueBot is under development since 2017, it targets systems to collect and gathering information of infected host to assistant in deploying more malware. The new version can load and execute more modules and shell codes.
How is it deliveried?
TrueBot is more commonly delivered via malicious emails, or with infected USB drives.
How to protect myself ?
1- First, the operating system and all software must always be up to date. 2- Deploy multi-factor authentication in order to avoid credential compromise. 3- Be careful with attachments you receive via email. 4- Avoid using USB drivers that might be suspicious. 5- Install Antivirus on your devices, and keep it up to date too.
Finally, always pay attention on what you do on the internet. If you notice any unexpected moves on your device, take it seriously and investigate carefully what might have happen. Trace and clean (reinstall the OS in some cases). The important thing is, do not neglect the issue.






